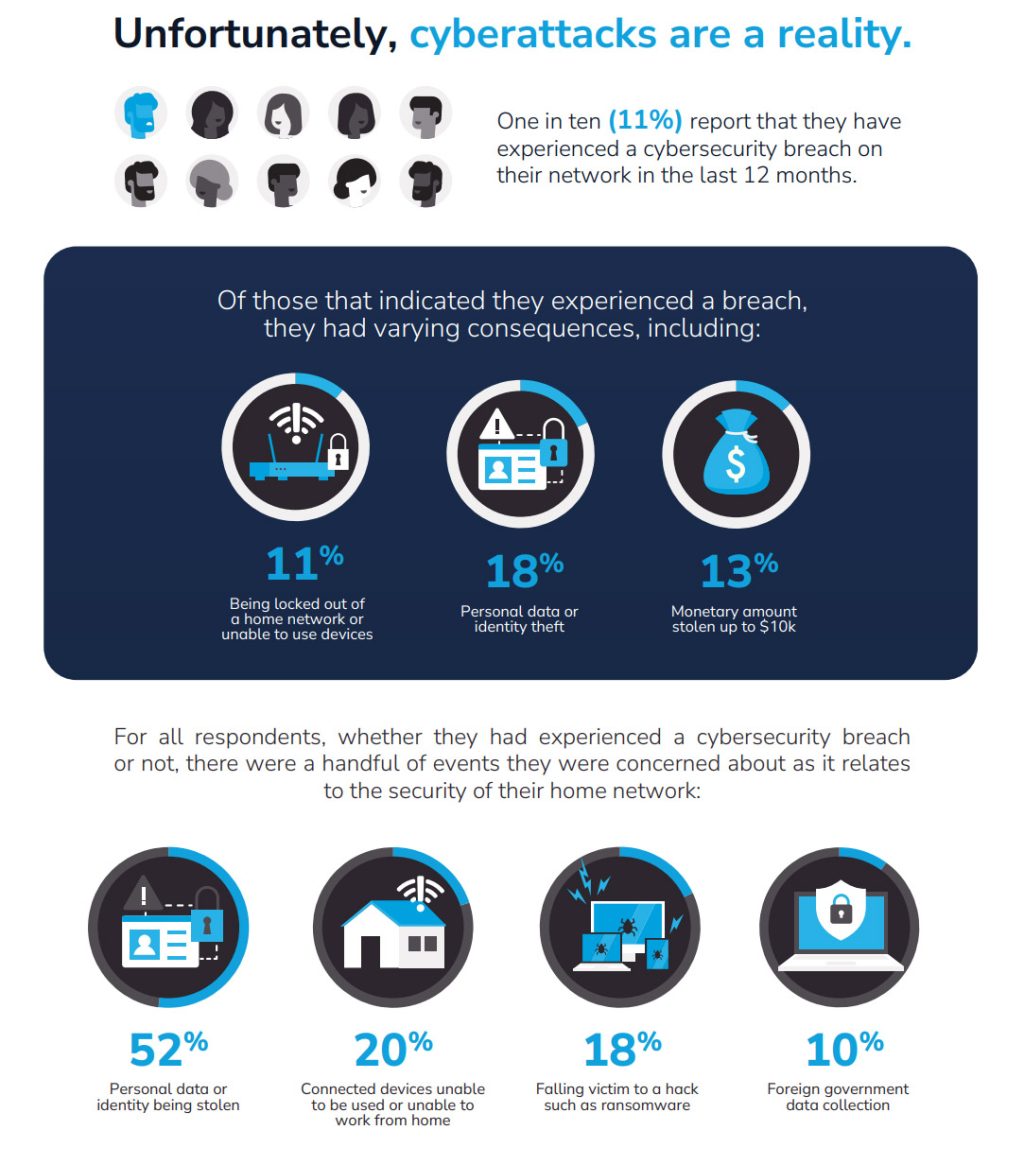
In today’s digital age, businesses rely heavily on technology to operate efficiently and effectively. However, with this increased reliance comes a significant risk: cybersecurity threats. These threats pose a major concern for businesses, as they can compromise sensitive data and disrupt operations.
The impact of cybersecurity threats on data protection cannot be overstated. A single breach can result in the loss or theft of valuable business data, including customer information, financial records, and intellectual property. This not only damages a company’s reputation but also leads to significant financial losses, as well as potential legal consequences.
Moreover, the consequences of a cybersecurity breach extend beyond the immediate impact on the business itself. In today’s interconnected world, breaches can have far-reaching effects, including affecting customers, partners, and even entire industries. For instance, if a company handling sensitive medical information experiences a breach, it could compromise patient confidentiality and put public health at risk.
So, what steps can be taken to protect against these cyber threats? The first line of defense is often considered to be cybersecurity awareness training for employees. Educating staff on the potential risks and consequences of phishing attacks, ransomware, and other types of malware is essential in preventing human error from becoming a vulnerability.
Another critical measure is investing in robust security software and firewalls that can detect and block malicious activity before it reaches sensitive data. Regular updates and patches for operating systems, applications, and other software are also vital to keep vulnerabilities at bay.
Furthermore, businesses must prioritize the implementation of secure data storage solutions and encryption methods to safeguard sensitive information both during transmission and at rest. This includes using two-factor authentication and implementing a secure password policy that balances ease of use with strength.
Additionally, businesses should consider partnering with reputable cybersecurity service providers who can offer expert guidance on threat detection and mitigation strategies tailored to their specific needs. Regular security audits and vulnerability assessments are also crucial in identifying potential weaknesses before they become major issues.
Finally, it’s essential for businesses to have a comprehensive incident response plan in place, which outlines the steps to be taken in the event of a breach or other cybersecurity incident. This should include notification protocols, emergency response teams, and procedures for restoring data and systems to a secure state.
By taking these proactive measures, businesses can significantly reduce their vulnerability to cyber threats and protect sensitive data from falling into the wrong hands.